I recently signed up with thinkbroadband for free Broadband Quality Meter (BQM) service. Once configured they send ICMP ping requests to my WAN IP address and collect the data to provide me with a picture of my broadband availability/ latency etc. They do all this for free and surface the data in a useful graph, which can be used to interpret various behaviours of my broadband connection, including the reliability of my provider!
So I set everything up, configured what I thought would be the appropriate firewall rules on my Unifi Security Gateway (USG) and left things for a day to start collecting data… or so I thought. When I checked back in the graph was a sea of red:
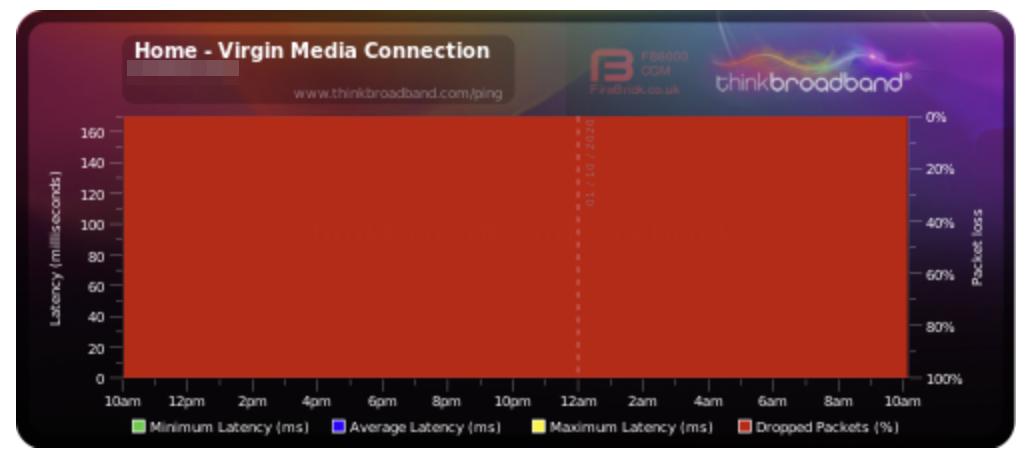
The red represents dropped packets, which were occurring at a rate of 100%. Turns out I’d specified the wrong kind of firewall rules! Having then done a bit of research it seems this is a common source of confusion for Unifi users, so I thought I’d document the settings I used to actually it working.
First off, I’m using a USG-3P running firmware version 4.4.51.5287926 and v6.0.23 of the Unifi UI.
Create a thinkbroadband Firewall Rule Group
To ensure that thinkbroadband are the only folks who can get an ICMP Echo Response from my network I created a Firewall Rule Group. This was a little trickier than I had expected, for reasons I shall explain…
thinkbroadband provide their egress CIDR range here. It is listed as 80.249.99.164/28, but the Unifi UI wouldn’t validate the value. I didn’t really question why and rather thoughtlessly converted it to a start-end format e.g. 80.249.99.160 - 80.249.99.175, which Unifi was content with.
It wasn’t until recently when a reader got in touch that I realised it isn’t a legal CIDR range: The 4 in the 164 is actually in the address, rather than the network segment (thanks Sean!). Having realised this I identified that the legal CIDR definition for thinkbroadband’s IP range is actually 80.249.99.160/28, which the Unifi UI is happy to accept as a valid CIDR.
Go to: Settings –> Security –> Firewall –> Create new Group
| Field | Value |
|---|---|
| Name | thinkbroadband.com ICMP check egress CIDR range |
| Type | IPv4 Address/ Subnet |
| Address | 80.249.99.160/28 |
One configured the group should look like this:
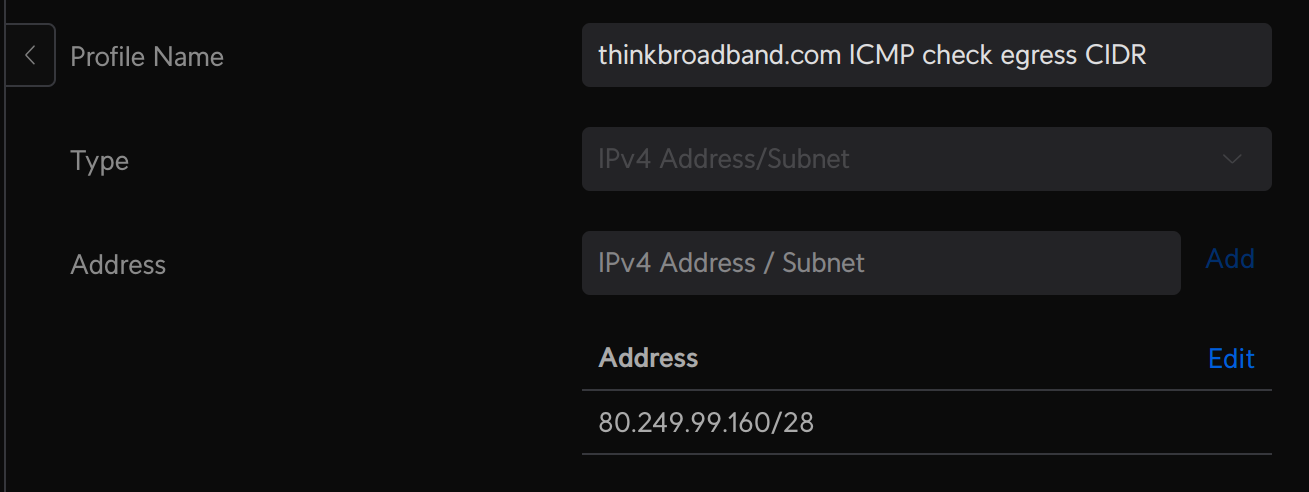
Save the group.
Create the Firewall Rules
The next step is to create the necessary firewall rules, one for ICMP Echo Requests and another for ICMP Echo Reply. I initially assumed that the requests rule should be an inbound “Internet In” type and that the reply rule should be an outbound “Internet Out” type rule, this however was not quite right.
For reasons I don’t fully understand both rules need to be configured as “Internet Local”, their details should be as follows:
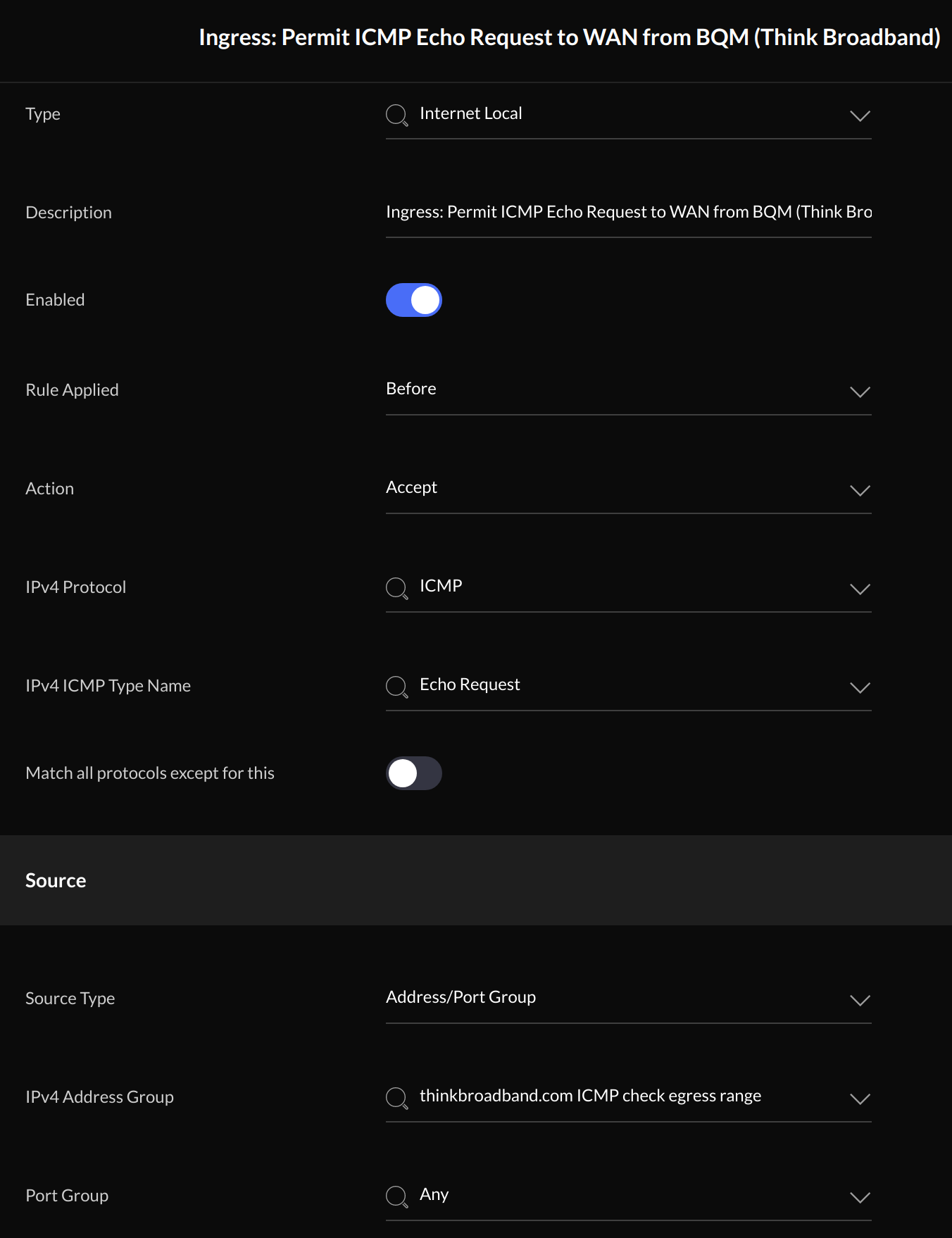
ICMP Echo Requests Rule
| Field | Value |
|---|---|
| Type | Internet Local |
| Name | Ingress: Permit ICMP Echo Request to WAN from BQM (Think Broadband) |
| Enabled | true |
| Rule Applied | Before |
| Action | Accept |
| IPv4 Protocol | ICMP |
| IPv4 ICMP Type Name | Echo Request |
| Match all protocols except for this | false |
Source
| Field | Value |
|---|---|
| Source Type | Address/ Port Group |
| IPv4 Address Group | thinkbroadband.com ICMP check egress range |
| Port Group | Any |
Once configured, the rule should look like this:
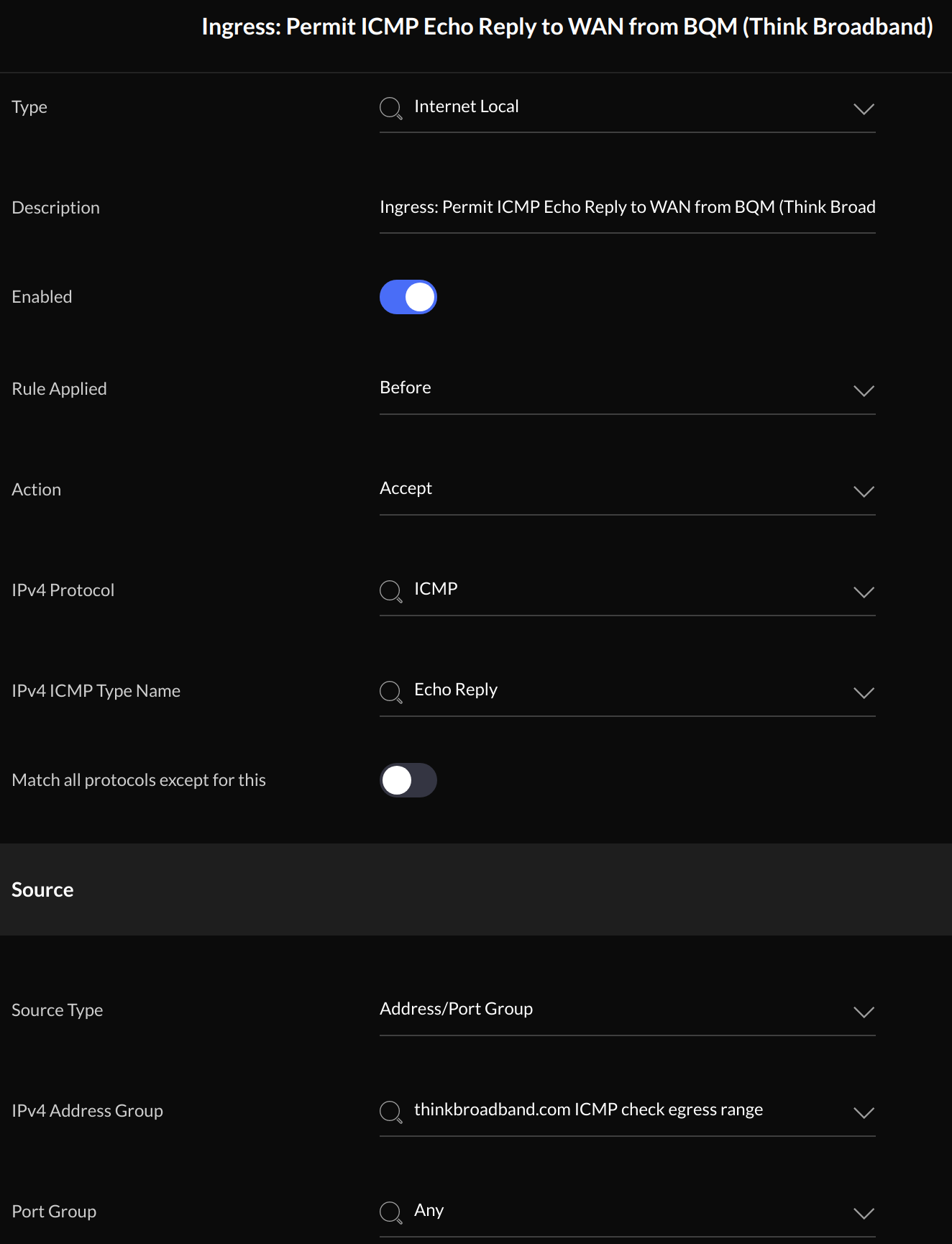
ICMP Echo Reply Rule
| Field | Value |
|---|---|
| Type | Internet Local |
| Name | Ingress: Permit ICMP Echo Reply from WAN to BQM (Think Broadband) |
| Enabled | true |
| Rule Applied | Before |
| Action | Accept |
| IPv4 Protocol | ICMP |
| IPv4 ICMP Type Name | Echo Reply |
| Match all protocols except for this | false |
Source
| Field | Value |
|---|---|
| Source Type | Address/ Port Group |
| IPv4 Address Group | thinkbroadband.com ICMP check egress range |
| Port Group | Any |
Once configured, the rule should look like this:
Back in the firewall section of the UI the new rules should appear as below:
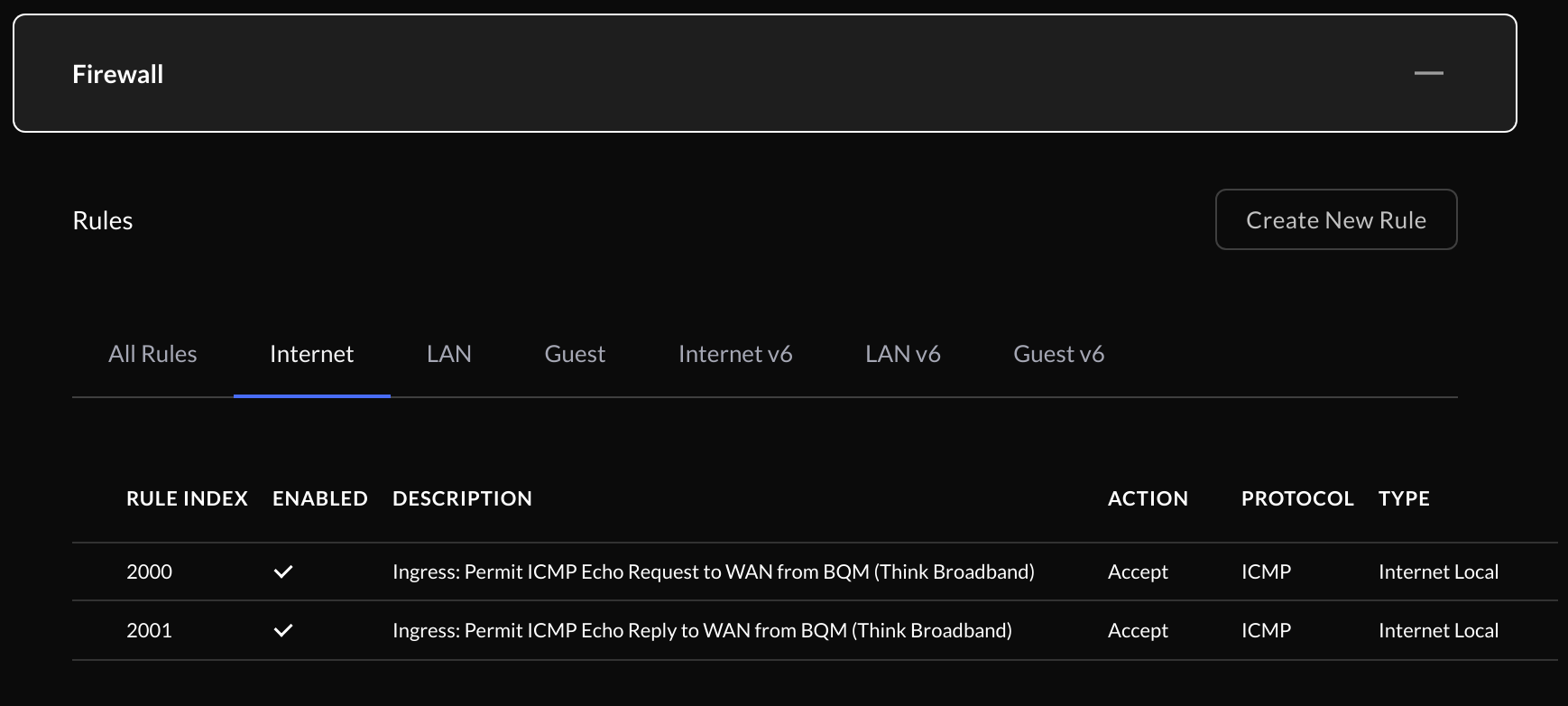
Testing
Having set up the firewall group and rules, I left things a while before checking back in on my BQM graph, which now looked like this:
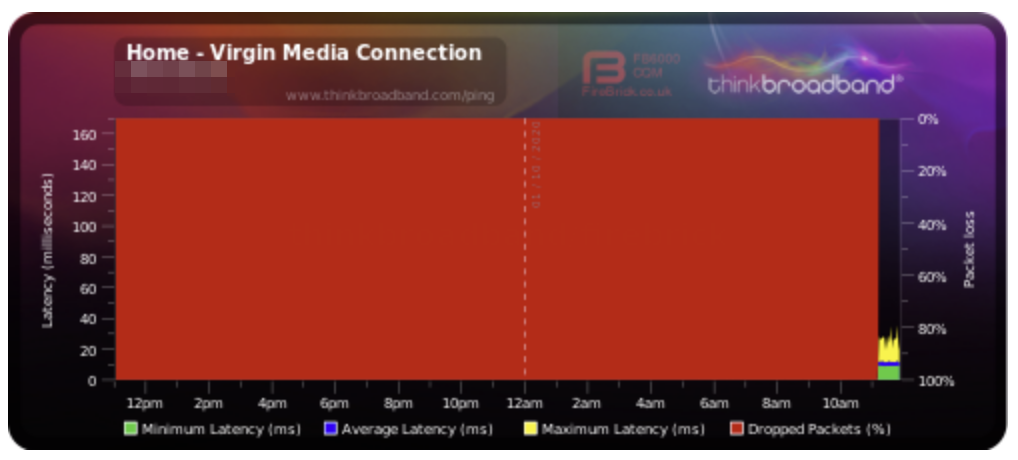
Great news! The traffic is now getting through.
Just one final test to ensure that ICMP traffic cannot get through from anywhere else. pentest-tools.com provides a free ICMP ping test which I used to confirm that no ICMP traffic was getting through from their test which, obviously, uses different egress IP addresses to thinkbroadband:
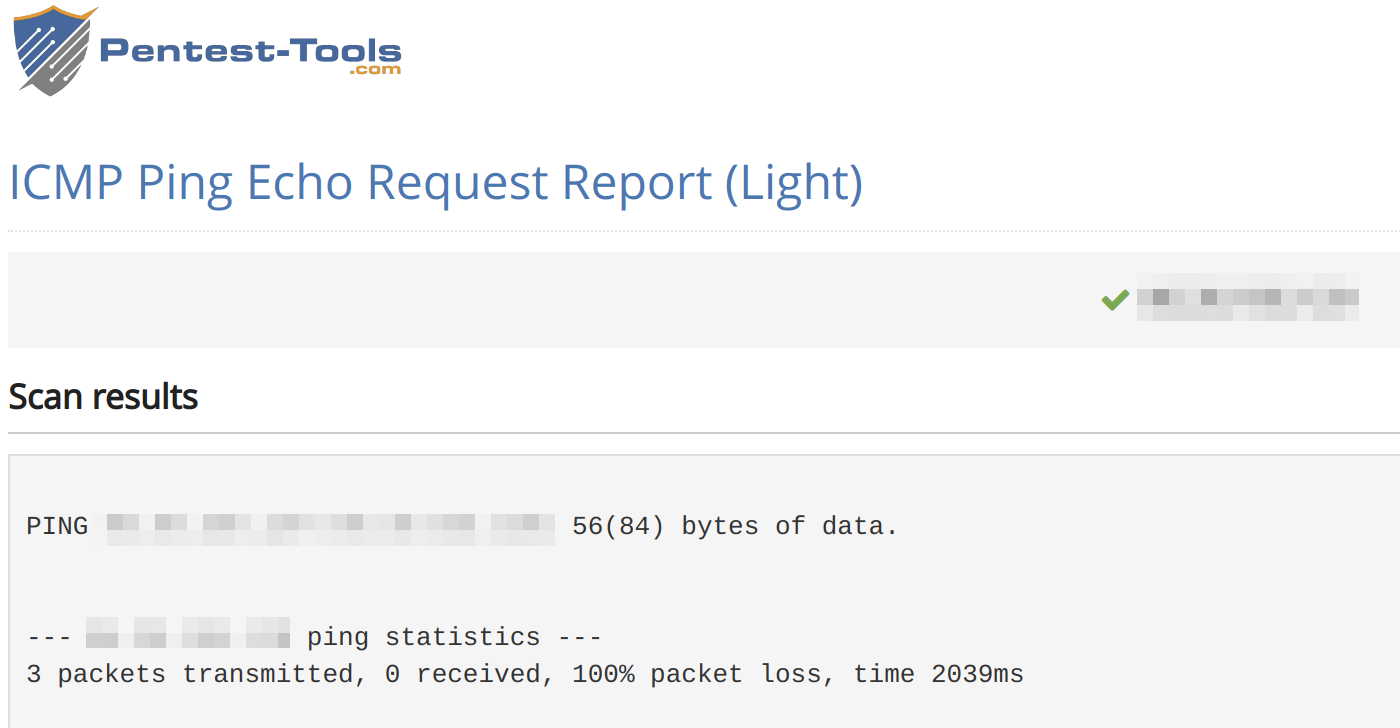
So that’s that, I can now use the BQM graph to help me observe various things, including when my ISP is playing up! I hope that this information is of use to someone.
Cheers,
Edd
Support:
If you’ve found my writing helpful and would like to show your support, I’d be truly grateful for your contribution.
